- Map shadow admins, unmanaged SPNs, stale accounts, and vulnerable configurations, without elevated privileges.
- Plant AI-recommended decoy accounts, SPNs, and objects to catch attackers early in their reconnaissance phase.
- Place realistic decoys to detect unauthorized domain traversal and stop escalation attempts in real time.
- Deliver high-confidence alerts on real attacker engagement—not logs or behavior models—to accelerate containment.
Active Directory Protection with Preemptive Cybersecurity
- Identify shadow admins and unmanaged SPNs.
- Monitor AD risk continuously without elevated domain rights.
- Predict adversary movement with automated analysis.
- Deploy decoys intelligently to preempt attacker logic chains.
- Reveal shortest attack paths to critical assets.
- Place decoys along likely traversal routes to disrupt movement.
- Trigger high-confidence alerts on real adversary engagement.
- Streamline response by integrating with SOC workflows.

See risks before attackers do.
- Identify shadow admins and unmanaged SPNs
- Map privilege paths without domain admin rights
- Continuously monitor for AD misconfigurations
- Prioritize exposures that attackers would exploit

Disrupt attackers before escalation.
- Analyze AD to find real-world attack paths
- Place decoys along traversal routes
- Detect ticket abuse and domain reconnaissance
- Block lateral movement toward domain control

Predict attacker movement automatically.
- Model attacker pathways across AD structure
- Automate decoy placement at key decision points
- Adapt dynamically to domain changes
- Eliminate manual tuning and blind spots

Act only on real threats.
- Trigger alerts on decoy engagement, not behavior guesses
- Integrate into SOC workflows for rapid containment
- Enrich detections with adversary behavior context
- Stop lateral movement before full domain compromise

- Expose Attack Paths with InSights™ Passively map AD configurations, shadow admins, stale accounts, and unmanaged SPNs, without domain admin rights or agent deployment.
- Deploy Deceptive Assets Across AD Acalvio recommends and places decoy users, computers, groups, and SPNs that attackers can’t distinguish from real assets.
- Detect Reconnaissance and Lateral Movement When attackers interact with decoy objects, high-confidence alerts are generated immediately—exposing credential theft, escalation attempts, or unauthorized traversal.
- Contain Threats with SOC Integration Seamlessly feed verified alerts into SIEM, SOAR, or EDR platforms for rapid investigation and automated containment.
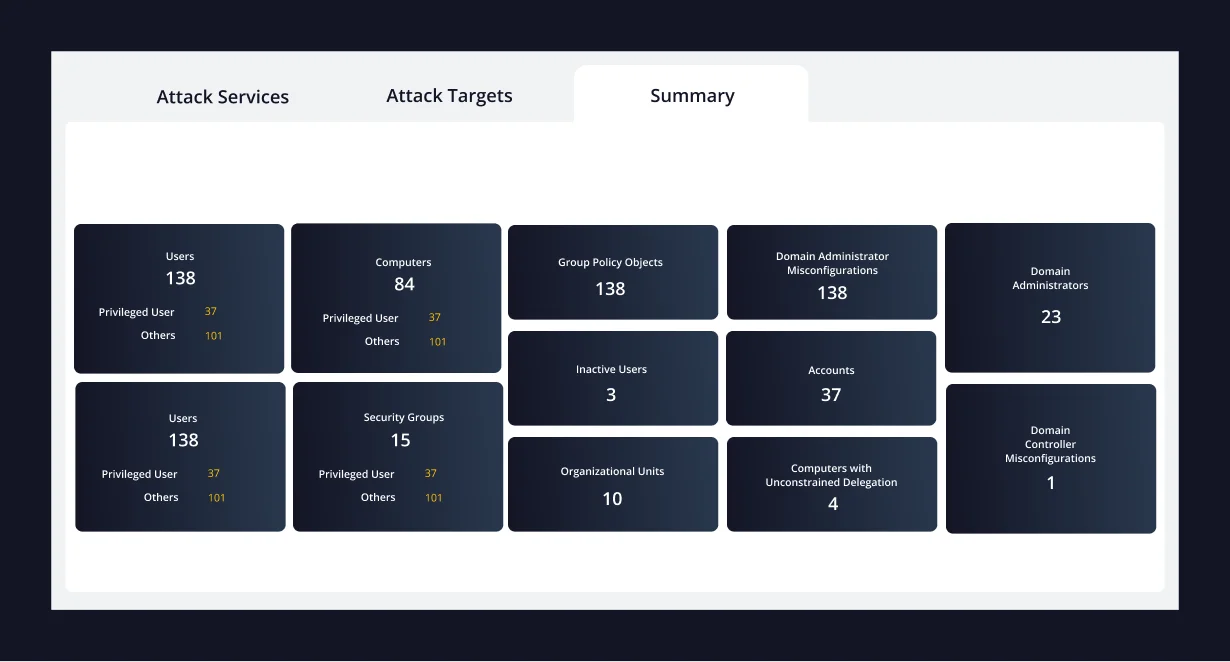
Builds an attacker’s view of your AD environment, exposing gaps before attackers exploit them. No domain admin rights or intrusive scans required. Key exposures include:
- Shadow admin accounts and over-permissioned users
- Kerberoastable accounts and unmanaged SPNs
- Orphaned and stale accounts creating hidden attack paths
- Misconfigured trusts, ACLs, groups, and GPOs
- Continuous visibility into attack surface across domains and forests
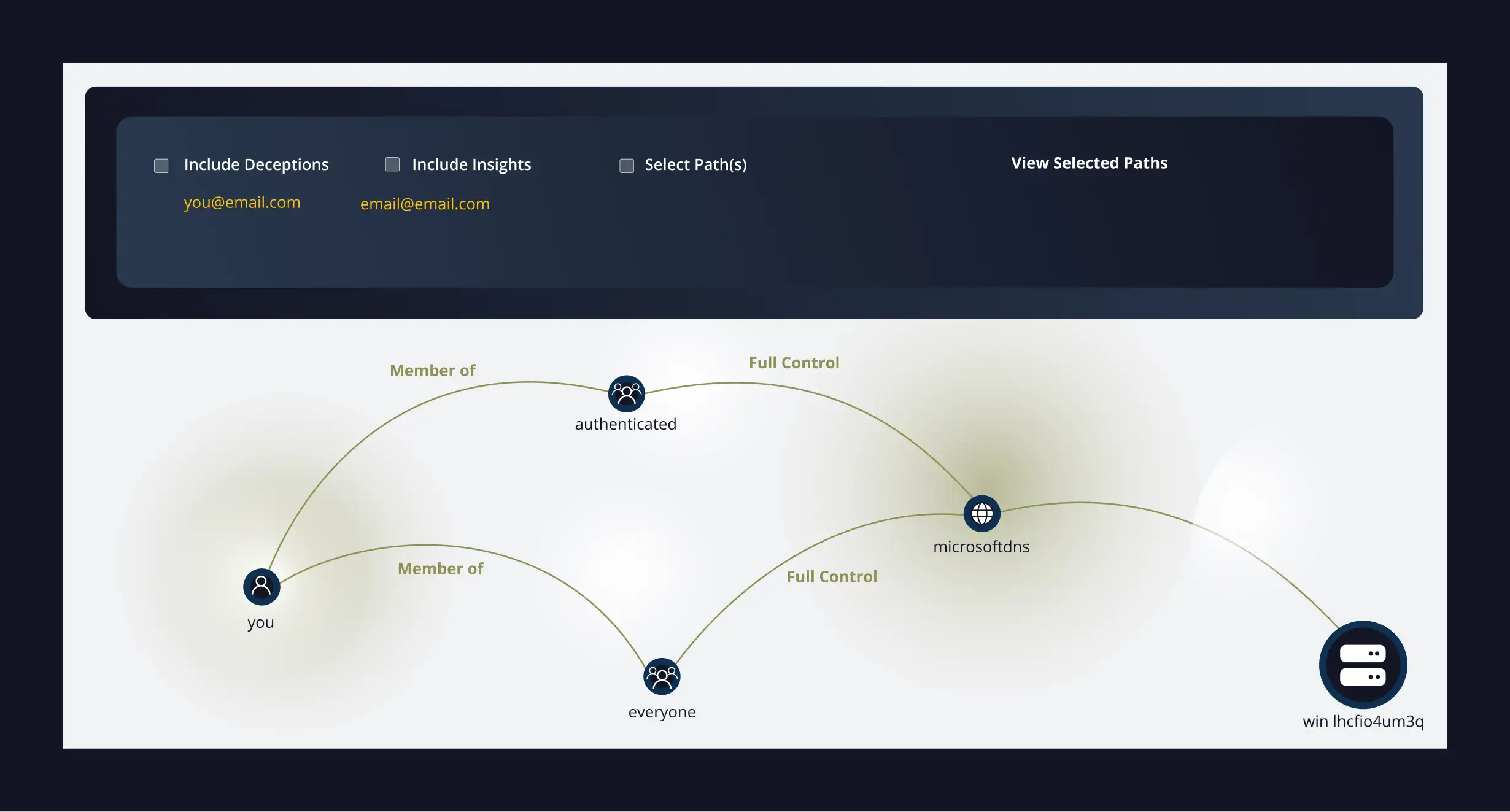
ShadowPlex maps potential lateral movement and privilege escalation paths an attacker would exploit inside Active Directory. Key capabilities include:
- Correlates relationships between users, groups, devices, and SPNs
- Identifies shortest attacker paths to domain dominance
- Highlights risky privilege escalation opportunities
- Enables security teams to proactively break attack chains
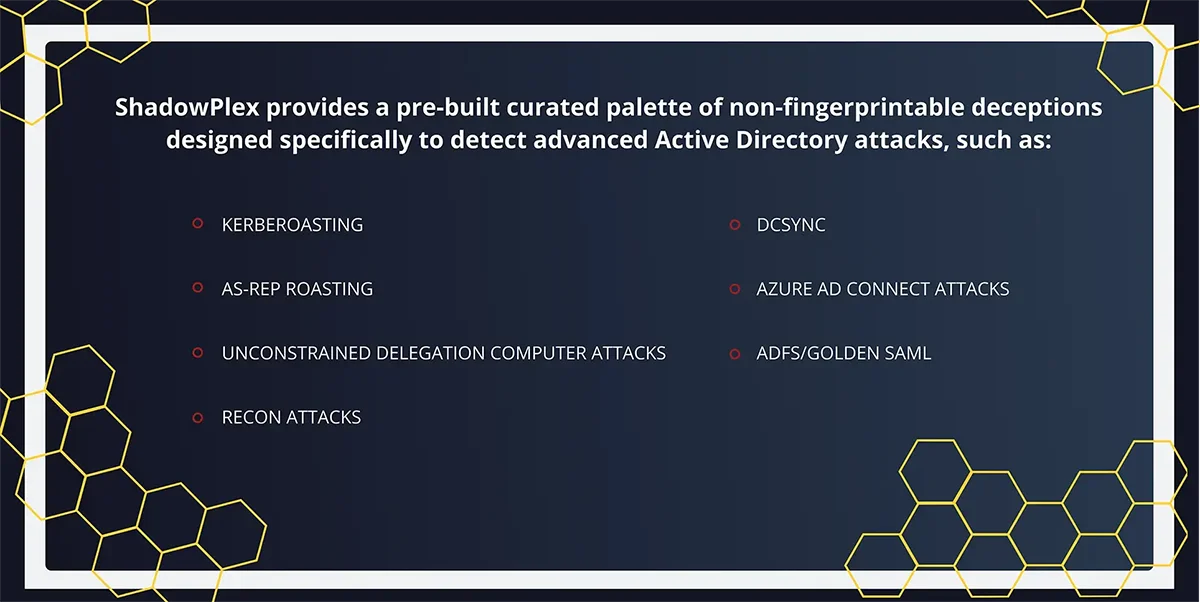
Acalvio Active Directory Deceptions: Targeted Defense, Powered by AI
ShadowPlex deploys purpose-built deceptions to detect and derail attackers before damage occurs:
- Prebuilt decoy objects for computers, users, services, and SPNs
- AI-guided recommendations for stealthy, realistic deception placement
- Detects Kerberoasting, AS-REP Roasting, DCsync, Recon, and Golden SAML attacks
- Seamlessly blends decoys into the production AD to avoid detection

ShadowPlex continuously adapts deception coverage to match AD changes:
- Uses AI to recommend realistic names, SPNs, and attributes
- Autonomously adjusts decoys as AD environments evolve
- Diverts attackers away from real assets toward decoys
- Removes the manual effort of ongoing deception maintenance
All decoy assets deployed by ShadowPlex are automatically hardened, preventing attackers from repurposing or pivoting from decoys to real production assets.
Immediately trigger high-fidelity alerts when attackers interact with decoy assets.
- Feed verified detections into SIEM, SOAR, or EDR tools for rapid response.
- Automate containment actions to isolate compromised endpoints or accounts.
- Prevent attackers from using decoy accounts or systems as footholds for further lateral movement inside production environments.
Built for Active Directory Security. Focused on Preemptive Defense
Continuously map misconfigurations, shadow admins, unmanaged SPNs, and stale accounts, without requiring elevated rights
Deploy decoy users, service accounts, and SPNs to attract attackers. Trigger high-fidelity alerts on intent-based interactions
Feed alerts to SIEM, SOAR, or EDR systems to rapidly isolate compromised endpoints and prevent production impact.



